 In this tutorial we will be showing you how to use Request Filtering in IIS to Prevent SQL Injections. We previously did a tutorial called, “How to block bots and spiders with Request Filtering,” and we will touch on a lot of the same concepts here.
In this tutorial we will be showing you how to use Request Filtering in IIS to Prevent SQL Injections. We previously did a tutorial called, “How to block bots and spiders with Request Filtering,” and we will touch on a lot of the same concepts here.
Please note that these instructions only apply to our Windows 2008 IIS 7 & Windows 2012 IIS 8 Servers.
First, you will need to make a connection to your site using IIS Manager. Please read our knowledge base article on How to connect to the server using the Microsoft IIS Manager.
Once connected:
Double click the Request Filtering module in IIS Manager.
Now click the URL icon in the Request Filtering module.
![]()
Next click Deny Sequence… in the “Actions” section.
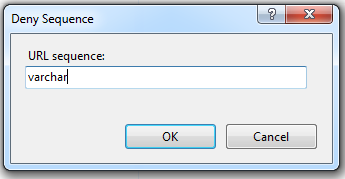
In this example we’ll be blocking the common SQL Injection term “varchar” so enter this in the Deny Sequence box and click OK.
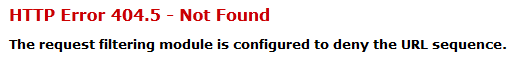
 So now when someone tries to enter “varchar” into your site’s URL, they will receive the follow error message from the server:
So now when someone tries to enter “varchar” into your site’s URL, they will receive the follow error message from the server:
There are a number of other terms that you can also use. Here are some terms you may wish to add to the Deny Sequence rules for your site account as well:
- @@version
- char
- exec
- execute
- declare
- cast
So now when anyone tries to enter any of the above terms into your URL Sequence, they will receive the HTTP Error 404.5 – Not Found error message from the server.
Be Warned! If your site currently uses any of the terms that you deny, you will receive the HTTP Error 404.5 message too. So choose your terms wisely to prevent any issues with your site.
<requestFiltering> <filteringRules> <filteringRule name="SQLInjection" scanUrl="false" scanQueryString="true"> <appliesTo> <clear /> <add fileExtension=".asp" /> <add fileExtension=".aspx" /> <add fileExtension=".php" /> </appliesTo> <denyStrings> <clear /> <add string="--" /> <add string=";" /> <add string="/*" /> <add string="@" /> <add string="char" /> <add string="alter" /> <add string="begin" /> <add string="cast" /> <add string="create" /> <add string="cursor" /> <add string="declare" /> <add string="delete" /> <add string="drop" /> <add string="end" /> <add string="exec" /> <add string="fetch" /> <add string="insert" /> <add string="kill" /> <add string="open" /> <add string="select" /> <add string="sys" /> <add string="table" /> <add string="update" /> </denyStrings> <scanHeaders> <clear /> </scanHeaders> </filteringRule> </filteringRules> </requestFiltering>
